ICAM Incident Investigation: A Summary for Newbies
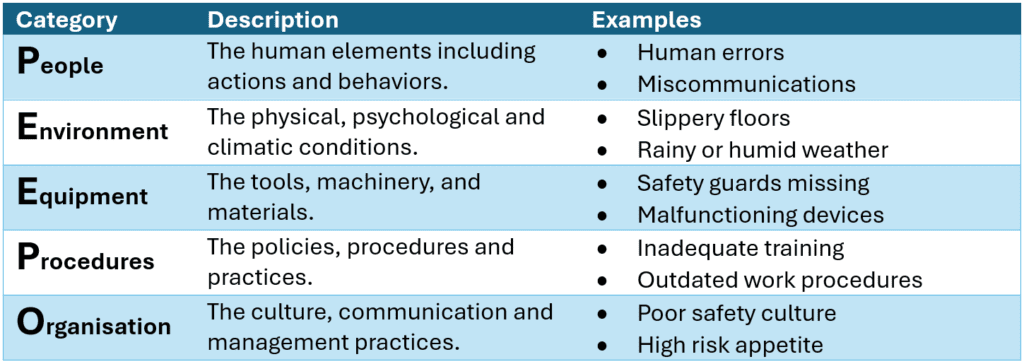
What is ICAM?
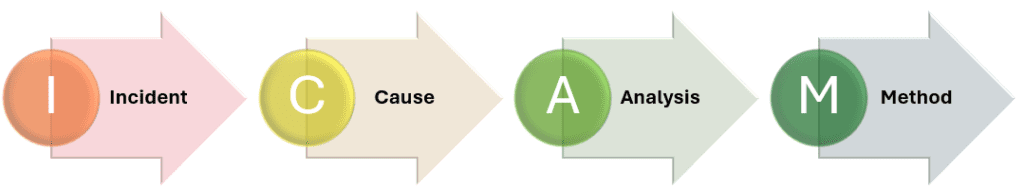 ICAM stands for:
ICAM stands for:
- Incident
- Cause
- Analysis
- Method
ICAM Investigation is a process that aims to identify the contributing factors, underlying (root) causes, and organizational failures that led to an incident. Rather than simply identifying the immediate cause, ICAM attempts to look deeper and detect the underlying (root) cause/s that led to an incident.
An example could be:
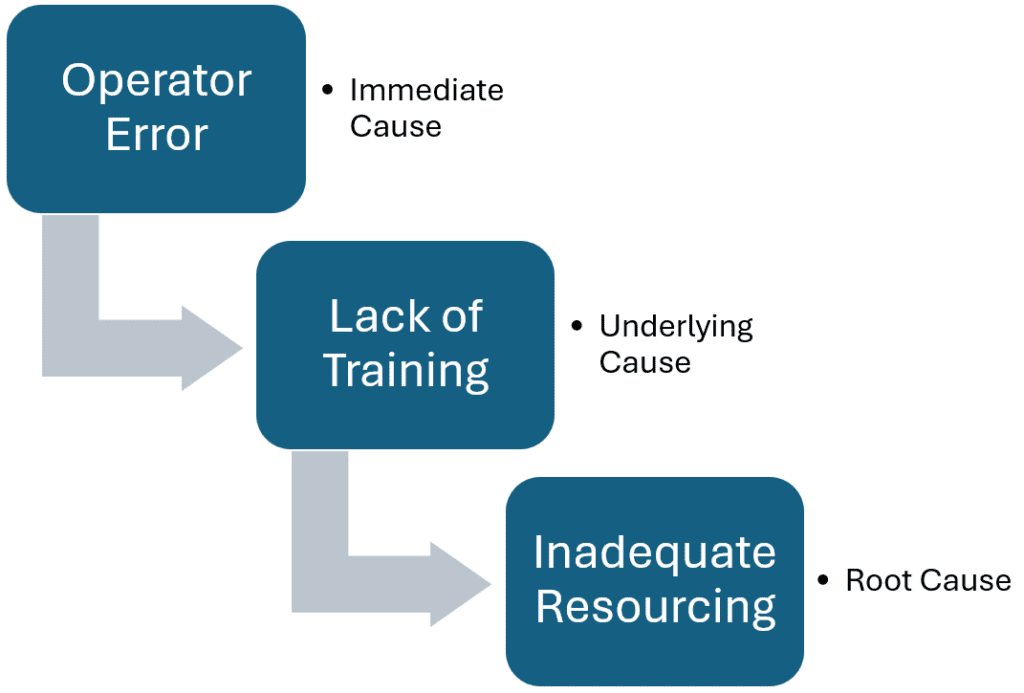 Sometimes the underlying cause may be uncomfortable for the organization to acknowledge, but it is vital these are identified and addressed to prevent reoccurrence and improve WHS performance outcomes.
Sometimes the underlying cause may be uncomfortable for the organization to acknowledge, but it is vital these are identified and addressed to prevent reoccurrence and improve WHS performance outcomes.
History of ICAM
In the 1990s, ICAM was developed by a group of individuals and organizations to evaluate existing incident investigation methods and develop a new method which incorporated the best features of each existing model. The resulting method “ICAM Incident Investigation” has become the go-to incident investigation model in Australia and internationally. This development was undertaken by (but not limited to):
- Gerry Gibb (CEO of Safety Wise)
- James Reason (Renowned Psychologist and Professor)
- Australian Transport Safety Bureau (ATSB)
What is the ICAM Process?
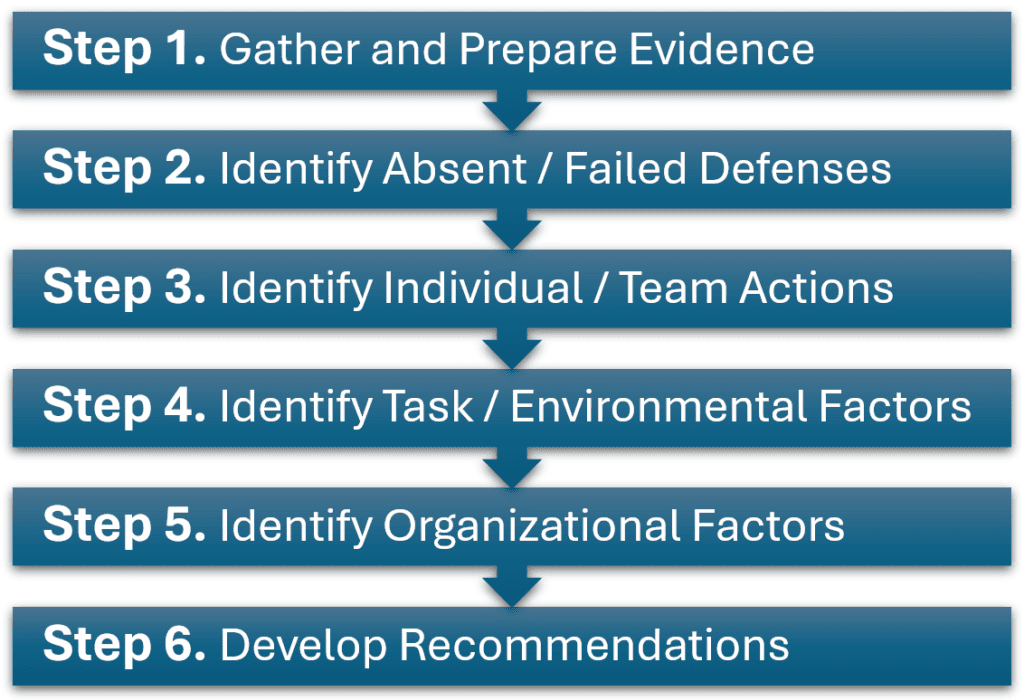
The ICAM Investigation process has 6 steps:
Download a copy of our simplified ICAM Incident Report and Investigation Form.
 We also provide free resources! Check them out:
We also provide free resources! Check them out:
- Free Policies
- Free Procedures
- Free Forms and Tools
- Free Plant Risk Assessments
- Free Verifications of Competency
*For internal use only. Not for resale or redistribution. By downloading, you agree to our Free Resources Licensing Agreement.
These document are templates only and it must be customised for your business. Other aspects that may need to be considered include, but are not limited to, ensuring that:
- Relevant legal requirements have been met,
- Workplace specific risks are identified and managed, and
- Workers are consulted with during the customisation / review process.
Step 1. Gather Evidence (PEEPO)
This step involves collecting all relevant information and evidence related to the incident, such as documents, video recordings and witness statements. Evidence are categorized into 5 groups using the PEEPO acronym.
Step 1. (cont’d) Analyze the Evidence
Analysis of evidence can be done with a variety of tools including:
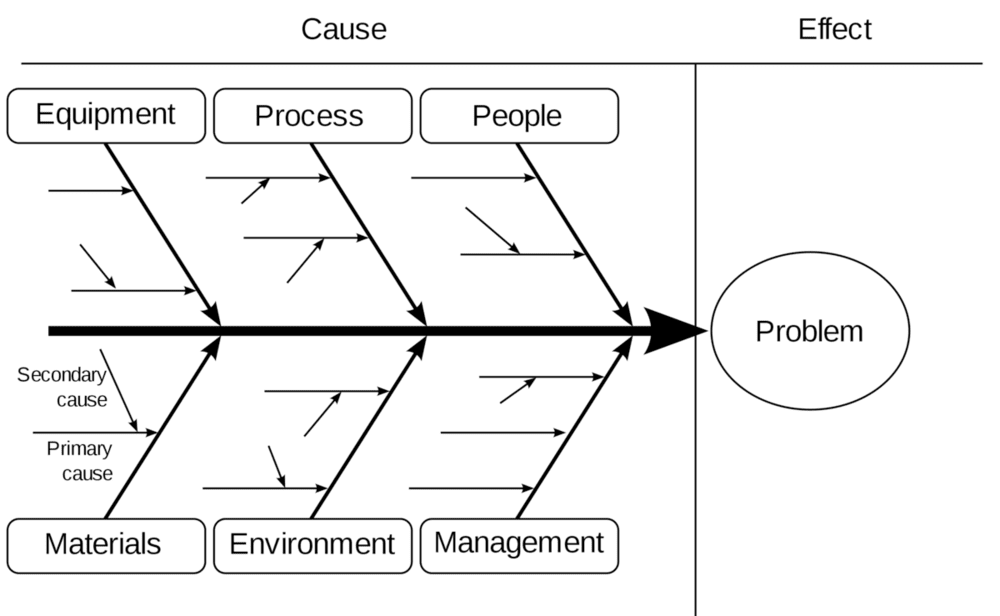
These tools help us to visualize all the gathered data and allow for easier analysis. Below is an example of an Ishikawa (or Fishbone) Diagram. This helps visualize how a number of contributing causes can lead to an incident (or “effect”):
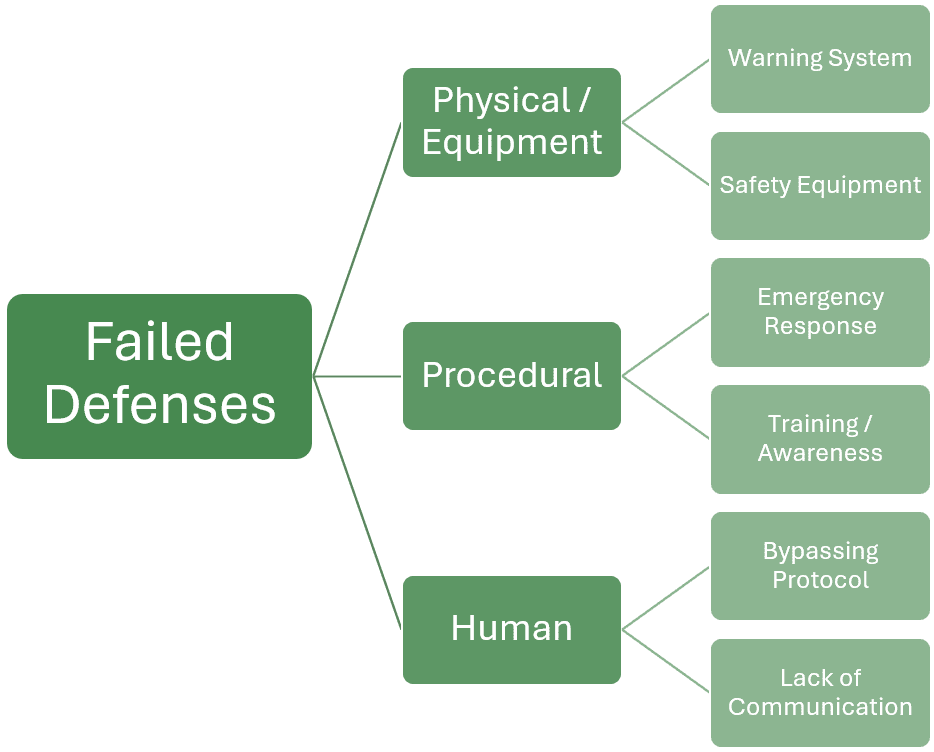
It is important to think critically and look deeper than the surface when examining these failed defenses. For example, identifying “human error in activating emergency system” as a failed defense may only be a symptom of a deeper and more systematic problem of “poor organizational training“ or other root causes.
Step 2. Identify Failed Defenses
This stage focuses on identifying the safety measures that were either not present or did not function as intended during the incident. It aims to uncover the last barriers that could have prevented the occurrence. To identify failed defenses:
List Existing Safeguards: Catalogue all intended safety measures, procedures, and equipment that were supposed to prevent the incident or minimize its impact.
Evaluate Functionality: Investigate whether these safeguards were in place and functioning as intended at the time of the incident.
Identify Gaps or Failures: Pinpoint specific defenses that were absent, failed to activate, were inadequately designed, or were not followed. This could range from malfunctioning equipment to ignored safety protocols.
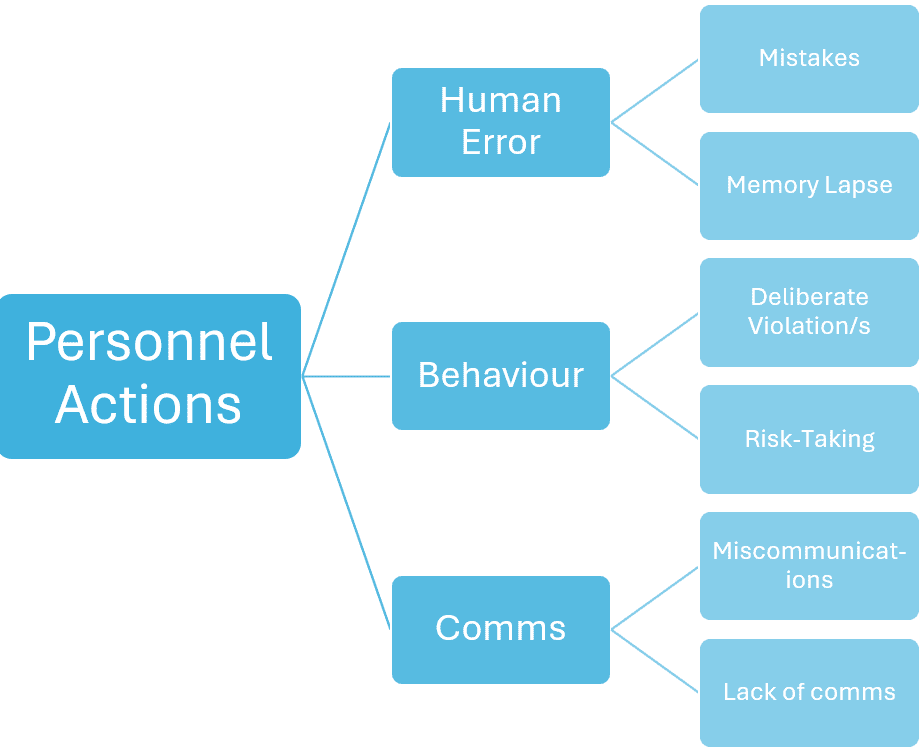
 Step 3. Identify Personnel Actions
Step 3. Identify Personnel Actions
In this step, the actions and decisions taken by individuals and teams involved in the incident are examined to identify any errors or violations that contributed to the event. To identify personnel actions:
Assess Competence and Training: Review the training, experience, and competence levels of all personnel involved.
Evaluate Behavior and Decisions: Look into the actions, decisions, and behaviors of the individuals before and during the incident.
Consider Human Conditions: Analyze human condition factors such as fatigue, stress, health, or personal issues that may be relevant.
Review Communication: Examine the effectiveness of communication among team members.
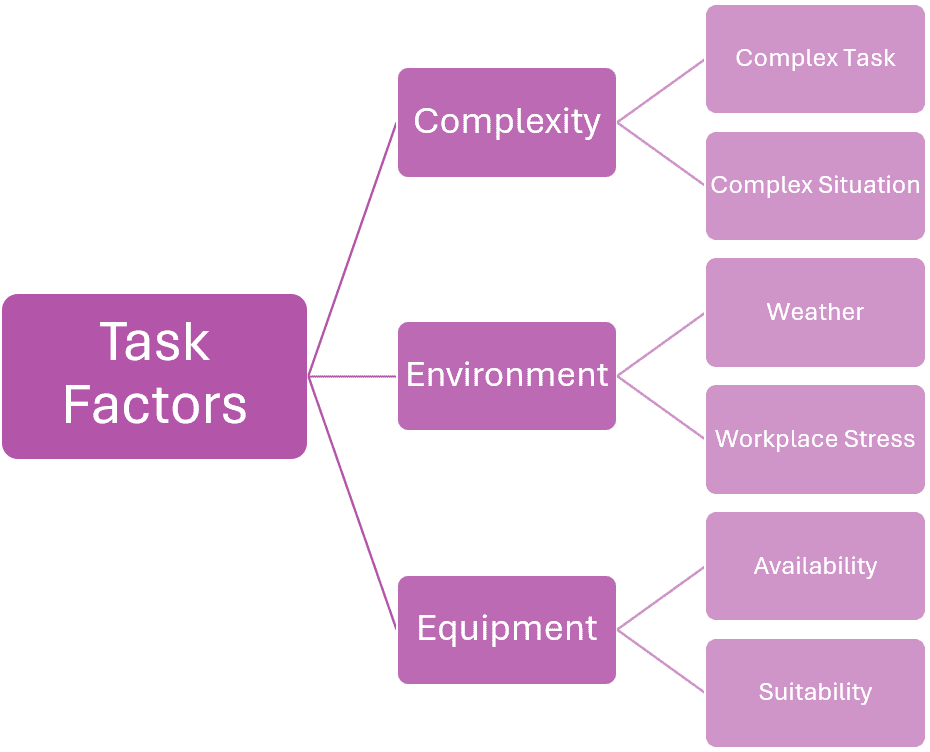
 Step 4. Identify Task Factors
Step 4. Identify Task Factors
This part of the process assesses the conditions under which the task was being performed, including any environmental factors that may have influenced the incident’s outcome. To identify tasks factors:
Break Down the Task: Decompose the task being performed at the time of the incident into its basic steps.
Review Procedures: Examine any existing procedures (SOPs), guidelines, or instructions.
Assess Conditions: Analyze the conditions under which the task was being performed (e.g. complexity or time pressure).
Identify Deviations: Look for any deviations from the planned procedures and understand the reasons behind these.
 Step 5. Identify Organizational Factors
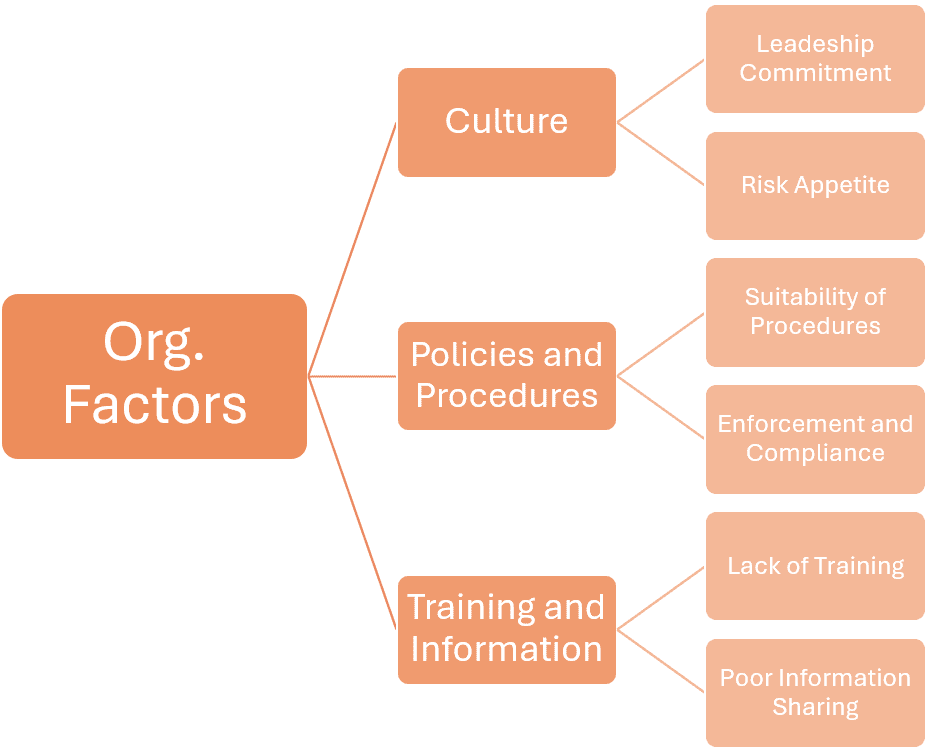
Step 5. Identify Organizational Factors
This step seeks to reveal underlying organizational influences, such as policies, culture, and systems, that could have indirectly contributed to the incident. To identify organizational factors:
Review Policies: Examine the organization’s policies and procedures.
Assess Safety Culture: Evaluate the overall safety culture within the organization (e.g. attitudes, behaviors, and practice).
Examine Communication: Look into the effectiveness and clarity of communication channels and practices.
Analyze Resources and Support: Determine if there were adequate resources (e.g., staffing, equipment, training).
 Step 6. Develop Recommendations
Step 6. Develop Recommendations
The final stage involves formulating recommendations based on the analysis to prevent future occurrences. To develop recommendations:
Address Root Causes: Ensure each recommendation specifically targets identified root causes.
Prioritize Safety: Focus on enhancing safety measures and preventing reoccurrence.
Consider Feasibility: Assess the practicality and cost-effectiveness of each recommendation.
Engage Stakeholders: Involve relevant stakeholders in the recommendation process to gain insights.
Be SMARTER: Your recommendations should comply with the SMARTER arconym.

What are the Benefits of ICAM?
ICAM incident investigations are open source and can be accessed and used by anyone. Also, the ICAM training (or ICAM Lead Investigator Course) can be delivered by any organization (or RTO) and is not “proprietary” or owned by any one company or entity. The ICAM Investigation process or further information can be researched freely on the internet meaning anyone with a laptop can teach themselves the ICAM investigation process.
ICAM has many benefits, with the main four benefits being:
- Improved evidence gathering (systematic and comprehensive)
- Effective information analysis (detailed and adaptable)
- Development of deeper understandings (underlying and root causes)
- SMARTER corrective actions (prevention focussed)
Due to its open-source nature, the process has been developed and fine-tuned by many organizations and has established itself as one of the most used and effective incident investigation techniques globally.
FAQs
Who should perform an ICAM investigation?
ICAM investigations should ideally be led by someone with a strong understanding of the ICAM principles and experience in incident investigations. This can include safety officers, risk management specialists, or external consultants trained in ICAM.
When should an ICAM investigation be initiated?
An ICAM investigation is recommended after any significant incident, accident, or near miss. The timing is crucial; starting the investigation promptly ensures that evidence is preserved and witnesses’ memories are fresh, which helps in the accuracy of the investigation.
Is training required to conduct ICAM investigations?
While a basic understanding of incident investigation principles can be helpful, formal ICAM training is highly recommended to conduct effective investigations. ICAM-specific training courses provide individuals with the knowledge and tools needed to carry out thorough investigations.
How long does an ICAM investigation take?
The duration of an ICAM investigation can vary widely depending on the complexity of the incident and the scope of the investigation. Smaller, less complex investigations might be completed in a few days, while more complicated cases could take several weeks or even months.
Can ICAM be used for all types of incidents?
Yes, ICAM is versatile and can be applied to a wide range of incidents, including industrial accidents, workplace injuries, environmental spills, and more.
Further Reading
- Notifiable Incidents in Australia: 4 Things You Need to Know (Spire Safety) <https://spiresafety.com.au/resources/notifiable-incidents-in-australia/>
- Incident Notification (Safe Work Australia) <https://www.safeworkaustralia.gov.au/safety-topic/managing-health-and-safety/incident-notification>
- What is a WHSMS (Work Health and Safety Management System)? (Spire Safety) <https://spiresafety.com.au/resources/what-is-a-whsms/>
- Work Related Deaths Per Year in Australia: Facts and Figures (Spire Safety) <https://spiresafety.com.au/resources/work-related-deaths-per-year/>
